General Forum Rules
1. Respect & Professional Conduct
Treat all members with respect and courtesy
No harassment, bullying, discrimination, or personal attacks
Disagree with ideas, not people - keep discussions constructive
No hate speech, offensive language, or inappropriate content
Respect different skill levels - we all started as beginners
2. Quality Content
Use clear, descriptive thread titles
Post in the appropriate category
Search before posting to avoid duplicates
Stay on topic within threads
No spam, advertising, or self-promotion without moderator approval
Use proper formatting and code blocks for technical content
3. Account & Privacy
One account per person
No impersonation of others or organizations
Protect your own privacy - don't share sensitive personal information
Respect others' privacy - no doxxing or sharing private information
4. Language & Communication
English & Sinhala are the primary languages (unless in designated areas)
Use proper grammar and spelling when possible
Avoid excessive use of caps, emojis, or text speak
No trolling, flame wars, or derailing discussions
5. Moderation
Moderator decisions are final
Report rule violations using the report button
Don't mini-mod (backseat moderate) - let moderators handle issues
Constructive feedback about the forum is welcome in Site Feedback
Cybersecurity Ethical Guidelines
1. Legal Compliance
All activities discussed must be legal in your jurisdiction
Only perform security testing on systems you own or have explicit written permission to test
Unauthorized access to computer systems is illegal and will result in immediate ban
Do not discuss or facilitate illegal activities
2. Responsible Disclosure
Follow responsible disclosure practices for vulnerabilities
Do not publicly disclose unpatched vulnerabilities or zero-days
Give vendors reasonable time to patch before disclosure (typically 90 days)
Coordinate with security teams when reporting vulnerabilities
3. Prohibited Content
Absolutely no posting of:
Malware, viruses, ransomware, or malicious code designed to harm systems
Working exploits for unpatched vulnerabilities
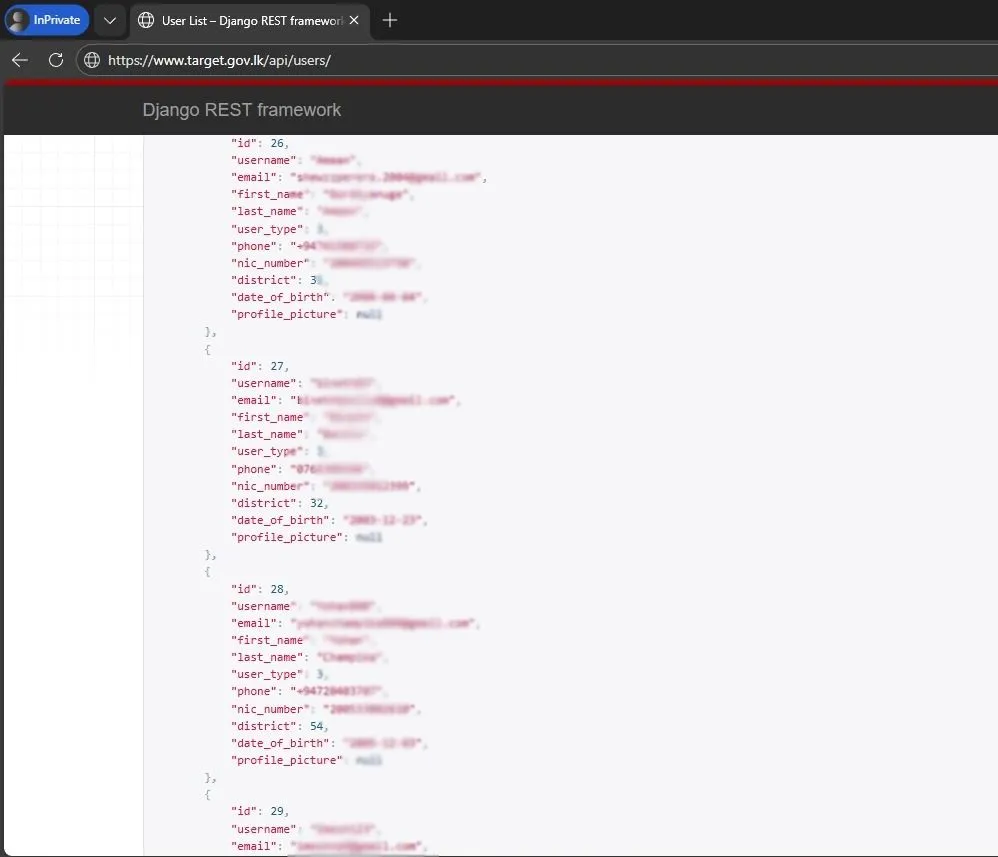
Personal data obtained without authorization (passwords, credit cards, PII)
Instructions for illegal hacking or unauthorized access
Phishing kits, credential stuffers, or fraud tools
Methods to bypass security for illegal purposes
4. Educational Purpose Only
All security discussions must be for educational and defensive purposes
Tools and techniques should be used to improve security, not compromise it
When discussing offensive security, always emphasize ethical boundaries
CTF writeups and lab exercises are encouraged
5. Vulnerability Discussion Guidelines
You MAY discuss:
Publicly disclosed CVEs with available patches
Theoretical attack vectors for educational purposes
Security research methodologies
Defensive strategies and mitigations
You MAY NOT share:
Private exploits or proof-of-concept code for active threats
Details that could enable attacks on unpatched systems
Information about targets without their consent
6. Penetration Testing Ethics
Always obtain written authorization before testing
Define clear scope and rules of engagement
Respect boundaries and stop if you find critical issues
Report findings professionally and responsibly
Do not access, modify, or delete data beyond what's necessary
7. Tool Usage Responsibility
Security tools are dual-use - use them ethically
Document legitimate use cases when sharing tools
Warn about potential misuse implications
Do not provide step-by-step instructions for malicious use
8. Data Handling
Do not share leaked databases or stolen credentials
Respect data privacy laws (GDPR, CCPA, etc.)
Use sample/dummy data in examples and tutorials
Properly anonymize any real-world examples
Consequences for Rule Violations
Warning System
First Offense: Written warning and content removal
Second Offense: Temporary ban (7-30 days)
Third Offense: Permanent ban
Immediate Permanent Ban
Sharing malware or malicious code
Posting illegal content
Doxxing or sharing private information
Coordinating illegal activities
Creating multiple accounts to evade bans
Serious Violations
The following will be reported to appropriate authorities:
Discussion or planning of illegal hacking
Sharing exploits for critical infrastructure
Child exploitation material
Terrorism or violence planning
Large-scale fraud schemes
Best Practices for Community Members
For Beginners
Read the stickied posts in each section
Use the search function before asking questions
Provide context when asking for help
Show what you've already tried
Thank those who help you
For Advanced Members
Be patient with beginners
Explain concepts, don't just give answers
Share knowledge generously but responsibly
Mentor others in their learning journey
Lead by example in ethical conduct
For Everyone
Think before you post: Would this help or harm someone?
Ask yourself: Is this legal and ethical?
Remember: Everything you post is permanent and may be seen by future employers
Stay curious: Security is always evolving - keep learning
Give back: Help others as you've been helped
Reporting Violations
If you see content that violates these rules:
Use the Report button on the post
Provide specific details about the violation
Do not engage with the violator
Let moderators handle the situation
For urgent security concerns or illegal activity: Contact moderators immediately via private message.
Contact Moderators
For questions about these rules or to appeal a moderation decision, contact the moderation team through:
Private message to moderators
Site Feedback section (for non-urgent matters)
By participating in this forum, you agree to abide by these rules. Ignorance of the rules is not an excuse for violations.
Last Updated: January 2026
These rules may be updated at any time. Check regularly for changes.
 1
2 Votes2 Posts156 Views
1
2 Votes2 Posts156 Views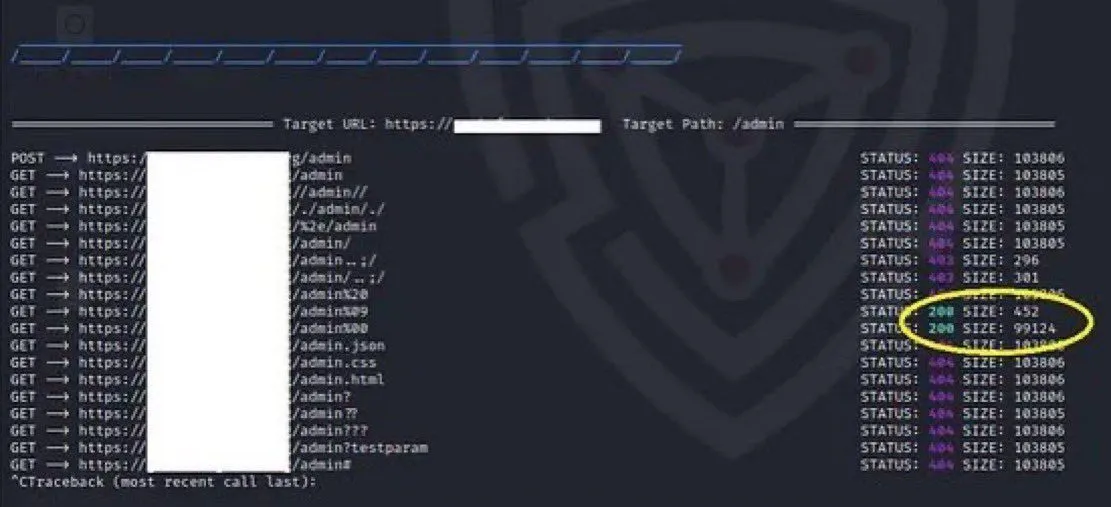 1
1 Votes1 Posts32 Views
1
1 Votes1 Posts32 Views 1
1 Votes1 Posts75 Views
1
1 Votes1 Posts75 Views